Today, we will discuss Azure AD Domain Services.
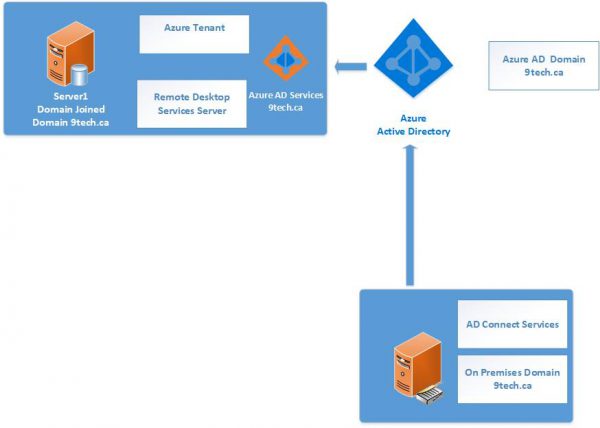
If you have a local on-premises AD, and you extended your domain to Azure AD using AD Connect, then all user accounts and groups are replicated to Azure AD and Office 365.
If you are using Exchange Online, Teams, etc., and want to set up a couple of servers in Azure that need to be part of your domain, then the question arises – how do you get those servers to join your domain?
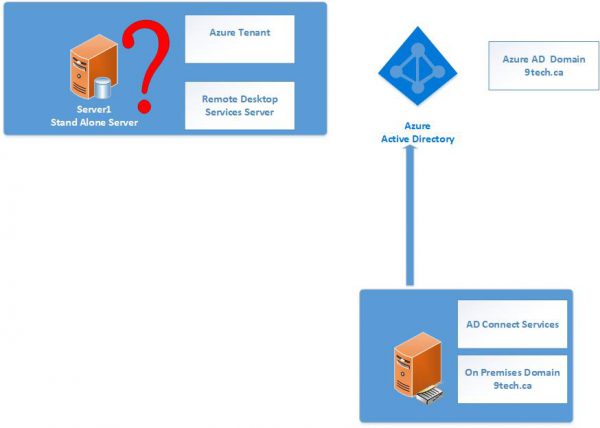
We have three options:
- Extend Local Network to Azure Network using Azure VPN Gateway, set up two domain controllers in Azure which are part of your existing on-premise Active Directory.
- Setup brand new domain on two domain controllers in Azure.
- Setup Azure AD Domain Service to replicate your internal domain to Azure
We will cover the third option where you can enable Azure AD Domain Services for their Azure AD tenant and choose to make domain services available in this virtual network.
All user accounts, group memberships, and user credentials available in your Azure AD tenant are also available in these new services.
When you configure AD Domain Service, setup will configure two domain controllers in Azure VNET. Those two domain controllers are part of your Azure AD.
Those two IP addresses are also your DNS EndPoint for your Azure VM.
How to setup Azure AD Domain Services
The next paragraph explains how to set up Azure AD Domain Services.
The only prerequisites are to have a dedicated subnet for Azure AD Domain Services.
To start setup navigate to your resource group and add Azure AD Domain Services
On Basic configuration blade, add your domain name.
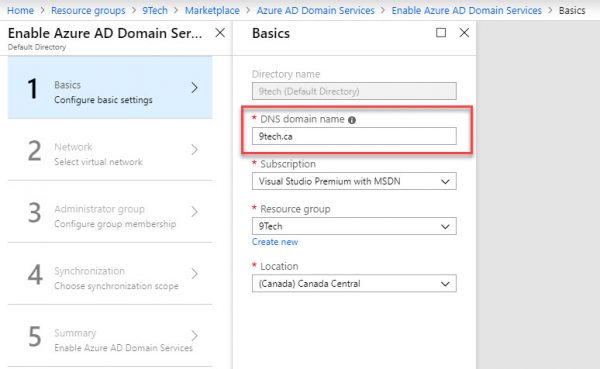
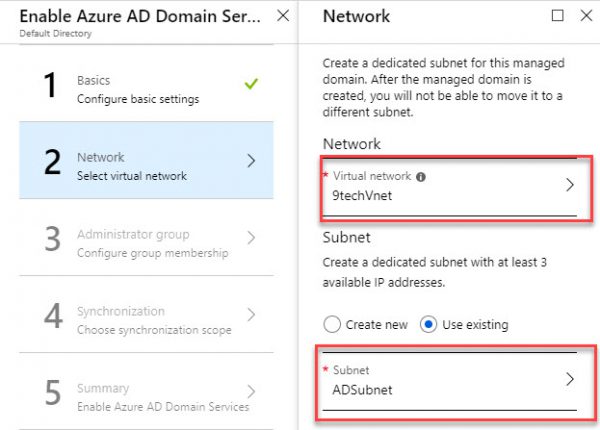
On Network page, add your Virtual Network and be sure you add a dedicated AD subnet.
The setting will create a new NSG group and apply to that subnet only.
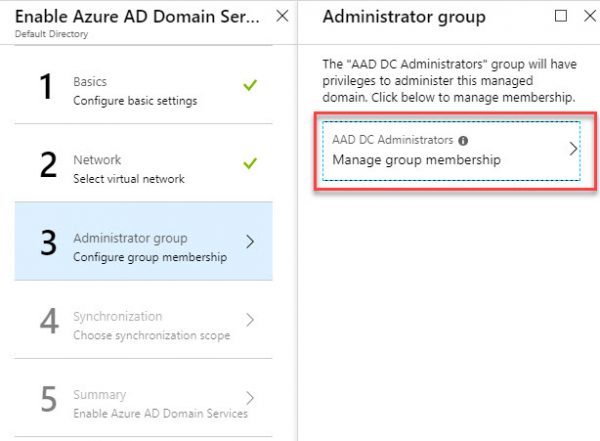
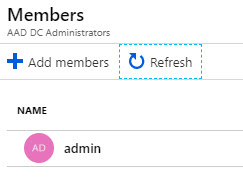
On the Administrator, Group page add an admin account.
Members of the AAD DC Administrators group are like Domain Admins in local on-prem AD.
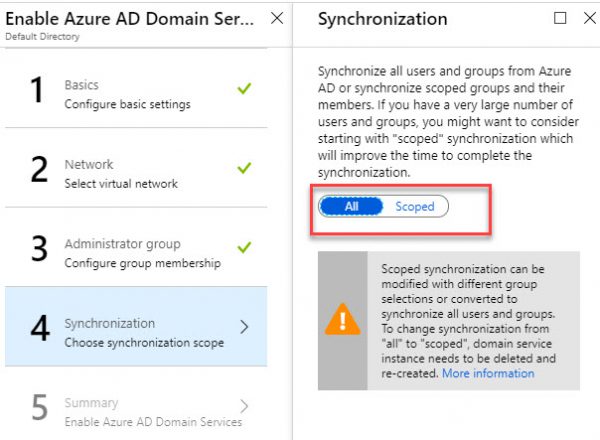
On the Synchronization page, choose default All Settings.
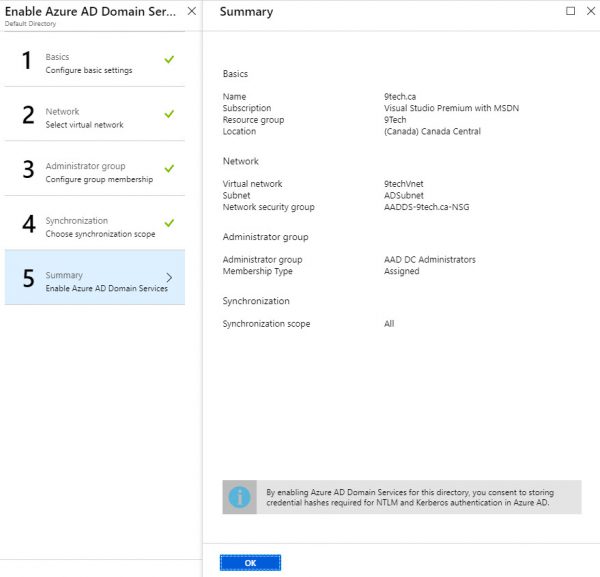
On the last page, you get a summary and after you select OK, Azure AD Domain Services will be configured in around 20 min.
After 20 minutes, Azure AD Services is up and running.
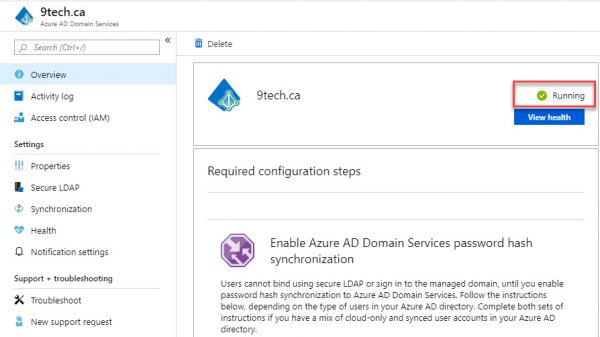
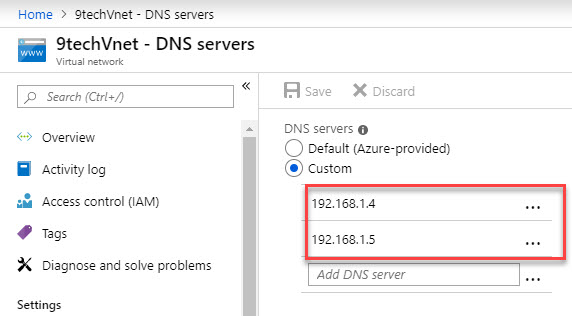
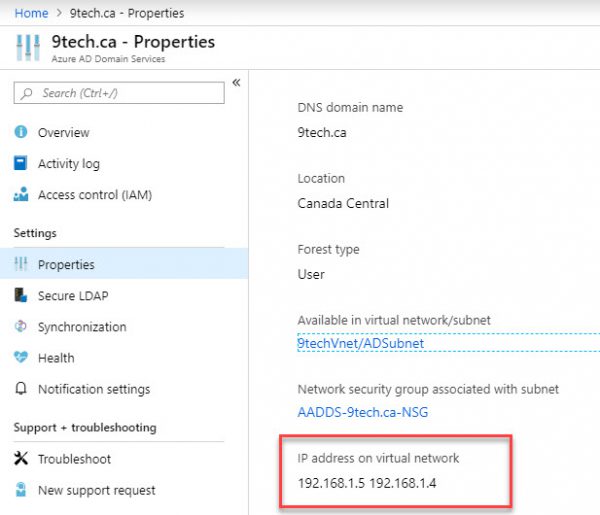
Navigate to the Properties Page and you will see two IP addresses listed.
Those are the IP address of the new AD domain servers.
We will need to pass those two IP address to our VNET DNS configuration.
All servers need to use these two DNS servers to be able to authenticate to the domain.
To authenticate users on the managed domain, Azure Active Directory Domain Services needs a password to be reset for all accounts (on-premises AD accounts or cloud-only accounts) accessing services in domain-joined servers in Azure.
This also applies to the administrative accounts part of AAD DC Administrators group. You will not be able to join a server to the domain before you change the password for an admin account.
Also, there is a waiting 20 min before all password change is replicated to Azure AD services.
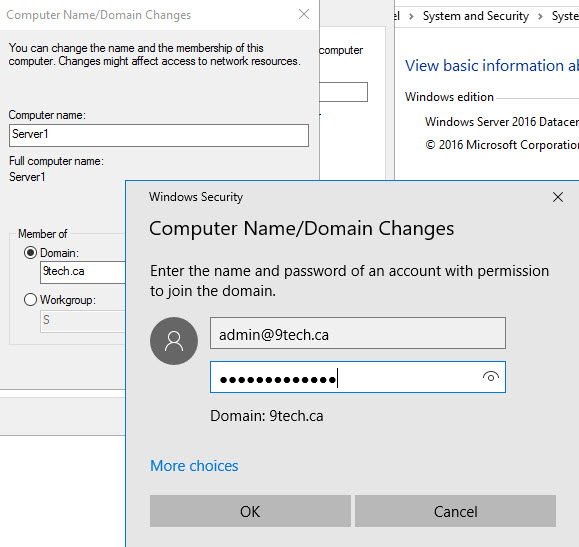
After we waited 20 min for the password server to propagate, we could join our server to the 9tech.ca domain.
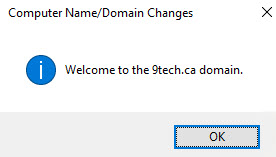
Server1 has been successfully joined to the domain.
Now you can see our server happily sitting in Azure, joined to our domain.
We can install the Active Directory Administration Tools on our server1.
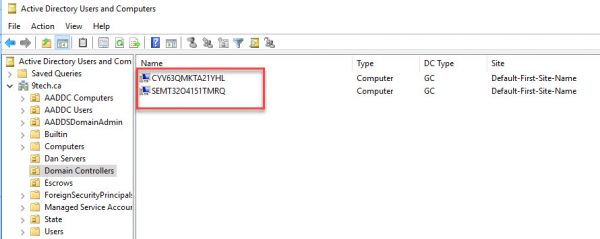
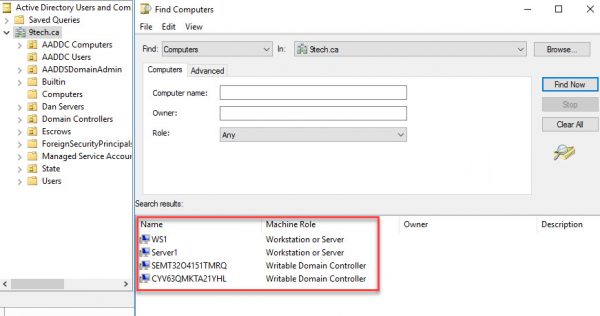
If you navigate to Domain Controllers, you will be able to see only two controllers provisioned to Azure AD services.
Local on-premises OU are not replicated to Azure AD Services but users and groups are.
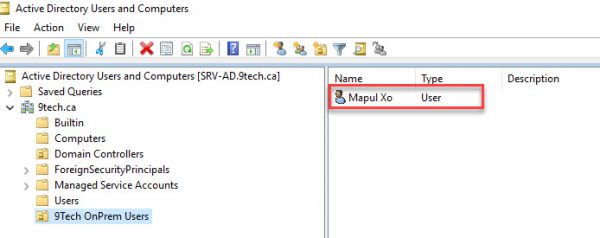
In the following figure, you can see the location of users on-premises AD.
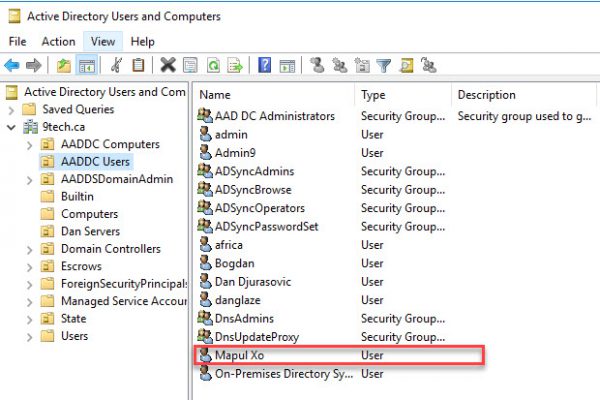
The very same user is located in AADDC Users OU in Azure AD Services.
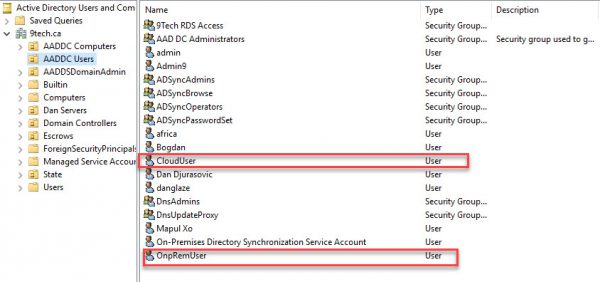
Let’s create two accounts.
We create CloudUser using Office 365 portal and we create a local on-premises user account called OnPremUser.
After 20 min both accounts will show up in AADDC OU.
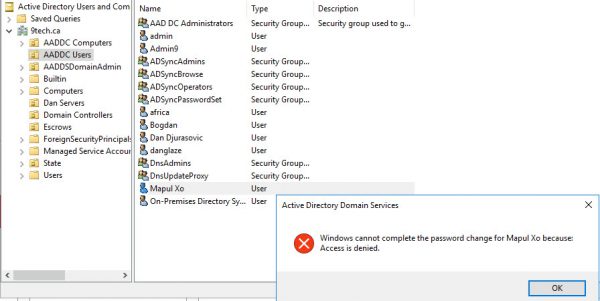
If we try to change the password for our users in Azure AD Services, we get Access is denied error.
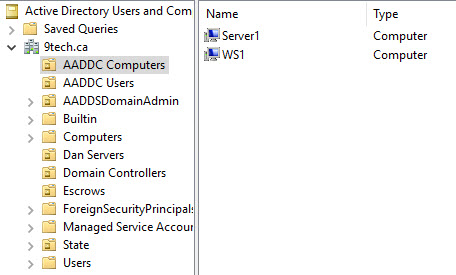
If we take a look at AADDC Computer OU, we will find the only computer objects what we joined them to Azure AD Services.
There are no on-premises computer objects replicated to Azure AD services.
If we search for computer objects in the Azure AD Services domain, we are getting only our Azure Server and two Azure AD Services controllers.
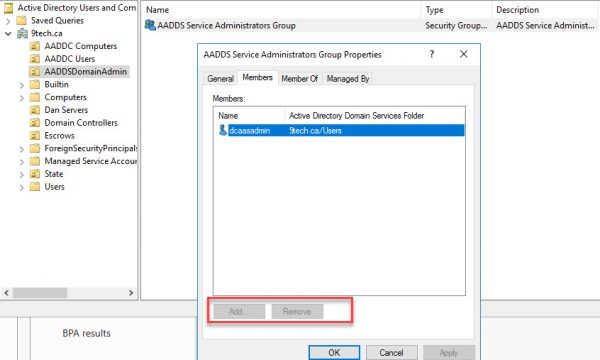
If we navigate to AADDSDDominAdmin OU and click on AADDS Service Administrators Group Properties, we will find some dcaasadmin accounts here.
This is some kind of account Microsoft is using it. We can not change the membership of that group
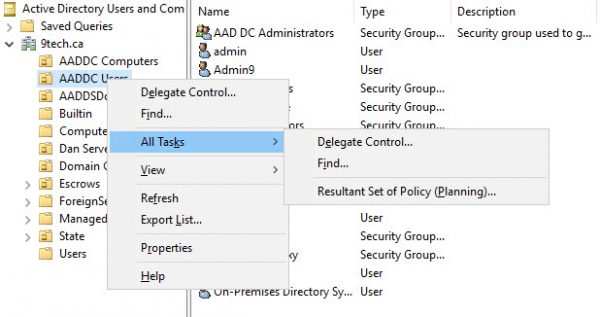
We can not provision any AD objects in the Azure AD Services domain as you can see on the following picture.
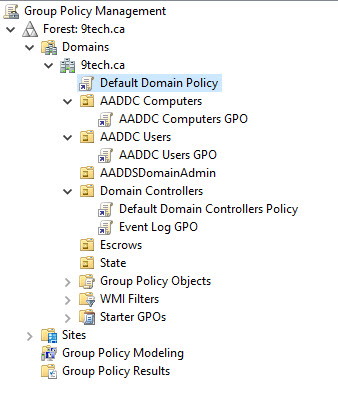
If we run Group Policies Editor we can see there are five preconfigured Group Policies
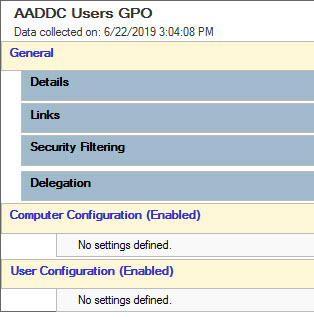
AADDC Users GPO is Empty
You can add new group policies only under AADDC Users and AADDC Computers.
Price
Azure Active Directory Domain Services usage is charged per hour, based on the total number of objects in your Active Directory Domain Services managed domain, including users, groups, and domain-joined computers.
The price for less than 25,000 objects is around CAD 140.16/month
I am hoping this blog will help you with evaluating and setting up Azure AD Domain Services.
/Dan
Hello good day,
I read this azure AD domain service with lot of interest. I am currently engaged in creating and running such a system for a company. I have been facing some issues in getting it working properly.
Is it possible for you to help me sort this out. I will appreciate your feedback. you can get to me using this private email: wegan.systems@gmail.com